Ethics in Product Design and Development
Build ethical considerations into your team's product development workflow through practical frameworks
Product teams face ethical questions daily: How does this feature affect user privacy? Does it cater to diverse users? Are we creating friction that protects users or frustrates them? These questions don't have universal answers, but they require intentional consideration. Ethical product development means creating space for these conversations before problems reach production.
The most effective approach integrates ethical thinking into existing workflows. Design reviews can include privacy considerations. Sprint planning can account for inclusive testing. Technical decisions can weigh long-term consequences alongside short-term gains. When ethics becomes part of how teams work rather than an afterthought, products better serve the people who use them.
Design reviews typically focus on usability, visual consistency, and business goals. Ethical design reviews add another layer by systematically examining potential harm, unintended consequences, and equity across user groups. These reviews happen at key decision points, not as a final checkpoint before launch.
Effective ethical reviews involve diverse perspectives. Include team members from different backgrounds, roles, and experiences. Use structured questions to guide discussion: Who benefits from this design? Who might be excluded? What assumptions are we making? What could go wrong? Document concerns and decisions so future teams understand the reasoning behind choices. Frame ethical concerns as questions, not accusations. "How might this affect users with X?" works better than "This is problematic for X.”
Start small by adding ethical considerations to existing review processes. Reserve 10 minutes in design critiques to discuss one ethical dimension, like accessibility or privacy. As the practice matures, develop a review framework specific to your product domain.
Privacy isn't something you add to a product after building core features. It's a foundational decision embedded in system architecture from the start. Privacy-focused architecture means choosing data models, storage solutions, and system integrations that minimize data collection, limit access, and give users control.
Start by questioning what data you actually need. Many products collect information "just in case" rather than for specific purposes. Map data flows through your system to identify where personal information travels, who accesses it, and how long it persists. Choose architectures that support privacy: local processing over cloud storage when possible, encryption by default, and clear data storing policies.
Technical choices reflect ethical priorities. Storing passwords as hashed values protects users. Building systems that can delete user data completely honors deletion requests. Creating separate databases for personal and operational data limits exposure. These decisions require upfront investment but prevent privacy problems that are expensive or impossible to fix later.
Pro Tip: Document why you collect each data point. If you can't explain its specific purpose, you probably don't need it.
Design sprints move fast, but speed shouldn't come at the cost of inclusion. Inclusive design sprints intentionally involve diverse participants and consider diverse users throughout the process. This means examining who's in the room making decisions and who's represented in the solutions being explored. Traditional sprints often include similar team members working through similar assumptions. Inclusive sprints expand participation to include people with different abilities, backgrounds, and experiences. Invite customer support team members who hear diverse user concerns. Include engineers who understand technical constraints that affect
Consider bringing in users from underrepresented groups as collaborators, not just research subjects. Structure sprint activities to support different working styles. Balance verbal brainstorming with silent ideation so introverts contribute equally. Provide materials in advance so participants can prepare. Use collaborative tools that work for remote and in-person team members. Test concepts with users who represent edge cases, not just your primary persona. Inclusive sprints produce better solutions because they surface problems and possibilities that homogeneous teams miss.
Dark patterns are interface designs that trick users into actions they didn't intend or make it difficult to do what they want.[1] These patterns prioritize business metrics over user well-being: hidden costs at checkout, confusing unsubscribe flows, pre-checked boxes for unwanted services, or interfaces that make saying "no" harder than saying "yes."
Detecting dark patterns in your own work requires honest evaluation. Many emerge gradually as teams optimize for conversion rates without questioning the methods. Review user flows with a simple test: Would this design work the same way if it benefited users instead of the business? Look for friction applied inconsistently, like making sign-up easy but account deletion difficult. Question defaults that favor the company, like opt-in settings for marketing emails.
Establish team practices that catch dark patterns early. Include "respectful design" as a design review criterion. Track support tickets that indicate user confusion or frustration with specific flows. Create space for team members to raise concerns without being dismissed as obstacles to business goals. The most effective detection happens when teams value user trust as much as conversion rates and understand that dark patterns create short-term gains at the cost of long-term credibility.
Technical debt refers to shortcuts taken during development that need fixing later. Ethical technical debt is similar but more serious: decisions that compromise user safety, privacy, or well-being to ship faster. Unlike regular technical debt, ethical debt can cause real harm while you're planning to fix it someday. Common examples include launching without proper security measures, skipping
Treat ethical technical debt differently than regular technical debt. Some things shouldn't ship incomplete, regardless of timeline pressure. Create a classification system that identifies which shortcuts are acceptable temporarily and which cross ethical lines. Document ethical debt explicitly so it doesn't get lost in backlog grooming. When timeline pressure forces difficult choices, be honest about tradeoffs and commit to specific remediation dates. Better yet, build enough buffer into schedules that teams aren't constantly choosing between shipping fast and shipping responsibly.
Pro Tip: If you wouldn't want users to know about a shortcut you're taking, it's probably ethical debt that shouldn't be incurred.
Security by design means building protection into products from the beginning rather than adding it after security incidents occur. This approach assumes threats will happen and designs systems that minimize damage when they do. Security becomes a design constraint like performance or
Start with threat modeling during early design phases. Identify what could go wrong: unauthorized access, data breaches, account takeovers, or malicious inputs. Security by design requires collaboration between designers, engineers, and security specialists throughout development. Designers create flows that encourage strong
Pro Tip: Design for security failures, not just success. What happens when someone gets unauthorized access? Limit the damage they can cause.
APIs enable products to share data and functionality with other services. For example, when a fitness app gets your step count from Apple Health, it’s using an API. When you expose your product’s API, you're deciding what data third parties can access, how they can use it, and what controls exist to prevent misuse. Poor API design can enable harm at scale, even if your own product behaves ethically.
Consider what happens when your API gets integrated into products you don't control. Rate limiting prevents abuse, but are your limits appropriate for legitimate use cases? Authentication protects data, but does your system verify that third parties have proper consent to access user information? Documentation guides developers, but does it explain ethical use alongside technical implementation? Many API providers focus solely on functionality without considering downstream consequences.
Establish clear terms of service that define acceptable use. Monitor API usage patterns to detect potential abuse early. Provide granular permissions so third parties only access data they genuinely need. Design endpoints that respect user privacy, like returning aggregated data instead of individual records when possible. Build tools that let users see which third parties access their data through your API and revoke access easily. Ethical API design recognizes that opening your system creates responsibility for how others use it.
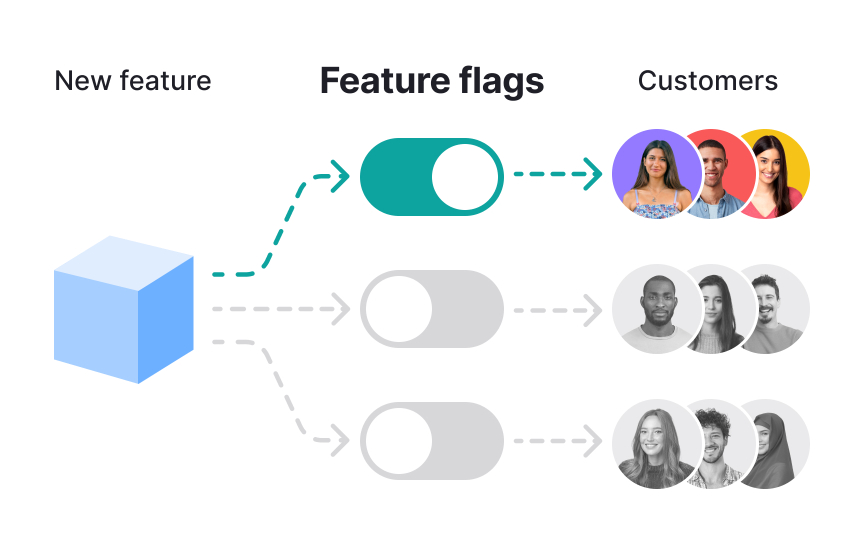
Feature flags let teams release features to specific user segments, test variations, or gradually roll out changes.[2] This technical capability creates ethical questions: Who gets access to new features first? Who gets excluded? Are you testing risky changes on vulnerable users? Releasing premium features only to high-value users creates inequality. Testing potentially problematic features on less-engaged users treats them as disposable. Running experiments without informing users that their experience differs from others raises consent issues. Geographic or demographic segmentation can inadvertently discriminate or reinforce biases.
To avoid these pitfalls, define acceptable criteria for segmentation and unacceptable ones. Document why specific user groups receive certain features. Consider whether users should know they're in a test group and obtain consent when appropriate. Avoid using feature flags to give advantaged users even more advantages while withholding improvements from those who need them most. Review flag strategies during sprint planning, not just implementation.
Launch criteria typically focus on performance benchmarks, bug counts, and business metrics. Ethical launch criteria add questions about user safety, fairness, and informed consent before releasing features to production. These criteria create a clear standard: some things don't ship until ethical concerns are resolved, regardless of timeline pressure.
Define what must be true before launch beyond technical readiness. Has the feature been tested with diverse users? Are privacy controls functional and understandable? Can users meaningfully consent to data collection? Does the feature create disproportionate harm for any user group? Are support systems ready to handle problems that emerge? Document these criteria explicitly so teams can't rationalize exceptions when deadlines approach.
Ethical launch criteria work best when integrated into existing release processes. Add ethical checkpoints to definition-of-done checklists. Include stakeholders beyond product and engineering in launch decisions: support, legal, and ethics specialists when available. Create a process for escalating concerns when teams disagree about readiness. Build organizational norms where delaying launch for ethical reasons is respected, not penalized. Shipping quickly matters, but shipping responsibly matters more.
References
Topics
From Course
Share
Similar lessons

Continuous Discovery Mindset

Business Outcomes vs. Product Outcomes